Powerful penetration testing tools and service for reliable security - all in one place
Harden and improve the security by discovering exploitable vulnerabilities in the security defenses with penetration testing tools and SolidPoint
Trusted Tools
Find security errors with manual Penetration testing tools and SolidPoint scanner. In SolidPoint we have automated most labor-intensive tasks with highly sophisticated tooling. Get access to SolidPoint used by pentesters and security professionals around the world.
Attacker Focused
Hunt vulnerabilities from the attackers perspective. Simulating real world penetration scenarios and proving impact for each security issue instead of presenting reports with false positives.
Manual pentest
Reports show that 80% of web applications are, in fact, vulnerable if checked manually. Real penetration testing are mostly done manually by highly skilled IT security experts. A manual pentest provides much more coverage and value.
Perfect automated penetration testing tools
Attack Surface
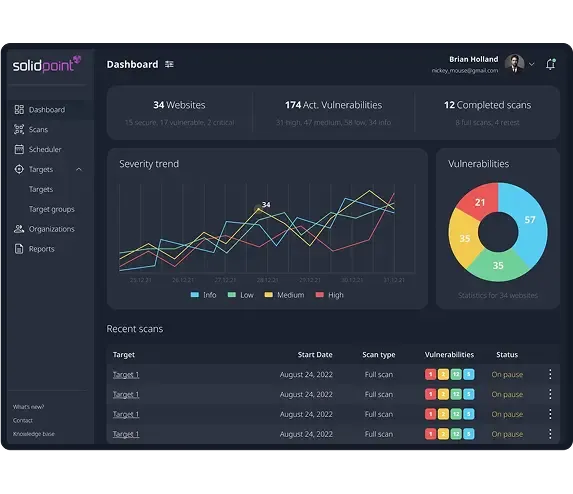
Vulnerability Assessment
Exploitation

Writing Penetration Testing Reports

Automate your Security Testing at Scale
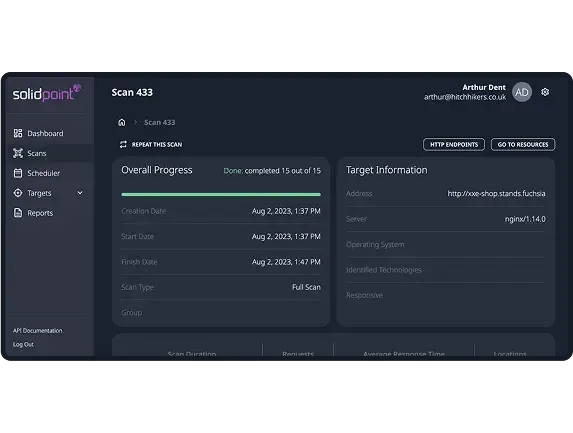
Why penetration testing tools from SolidPoint
We have over 10 years of manual pentest experience in a highly competitive market. We have automated most labor-intensive tasks with highly sophisticated tools. Now we can offer comprehensive web application penetration testing for an affordable price.
Quick problem solving.
Reports with zero false positives give team leads and developers all the information they need to quickly manage and fix each issue
Comprehensive report.
Receive a comprehensive report compiled by our security experts, with zero false positives and an accurate severity rating for each finding
Clear steps.
Help developers fix issues fast with clear reproduction steps and detailed recommendations based on our years of security experience
Saves time with automation.
SolidPoint makes it easier to automatically perform common repetitive tasks (e.g. find all web ports and run a web application scan on each one) Schedule SolidPoint to run periodically and automatically send scan results to external systems (Email, Slack, Webhooks, etc.) based on customizable rules
Complimentary retest.
Get a complimentary retest by our security experts to be 100% sure that the issue is resolved
Experience
We have over 10 years of manual penetration testing experience in a highly competitive market. We offer the first-ever cost-effective web application continuous penetration testing.
Find the problem
Our methods and tooling proved effectiveness on real world applications at bug bounty programs. Where lots of experts missed security issues, our approach revealed ones.
Fast and reliable
We have a track record of finding 0-day vulnerabilities in common software like WordPress, VMWare, etc.
FAQ
Penetration testing tools are software used to identify vulnerabilities in systems and networks.
It is recommended to conduct testing regularly, especially after significant changes in the infrastructure or software.
Vulnerability scanning, exploiting vulnerabilities, collecting information about the system, generating vulnerability reports.
Yes, many tools offer automated functions, but manual testing is also important to identify complex vulnerabilities.
Identifying vulnerabilities before they can be exploited by attackers, improving the overall security of the system, compliance with the requirements of regulations and standards.
Why SolidPoint
Cost-Effective
Free for smaller projects and paid once for larger ones.
High Performance
Penetration testing tools proven the high accuracy and speed.
Regular Updates
We work continuously to improve our service.
Customer-Focused
We've got all your needs covered.